mirror of
https://github.com/coder/coder.git
synced 2025-07-12 00:14:10 +00:00
#37 implemented the Sign-_in_ flow, but there wasn't a Sign-_out_ flow as part of that PR (aside from letting the cookie expire... or manually deleting the cookie...), which is obviously not ideal. This PR implements a basic sign-out flow, along with a very simple user dropdown: 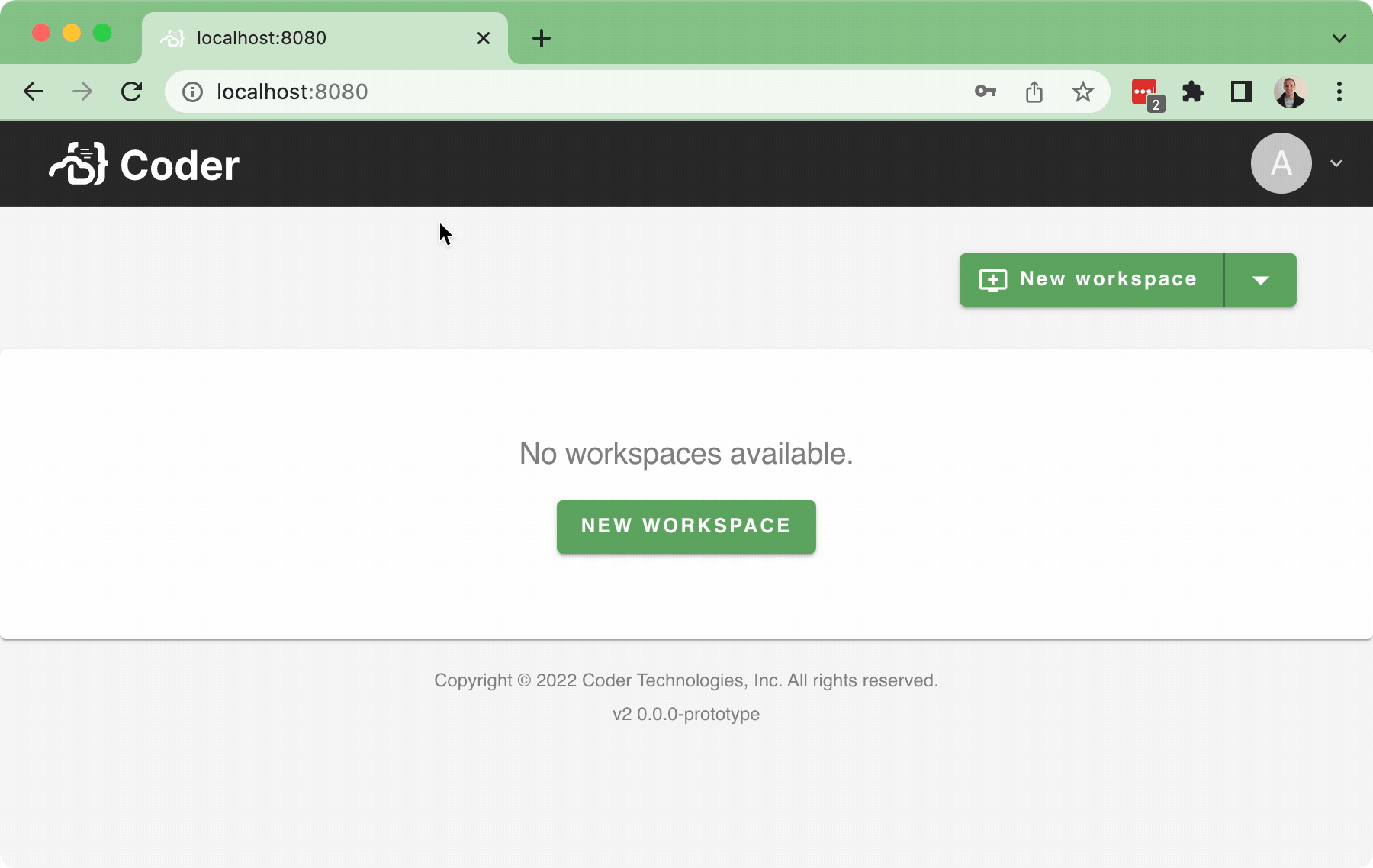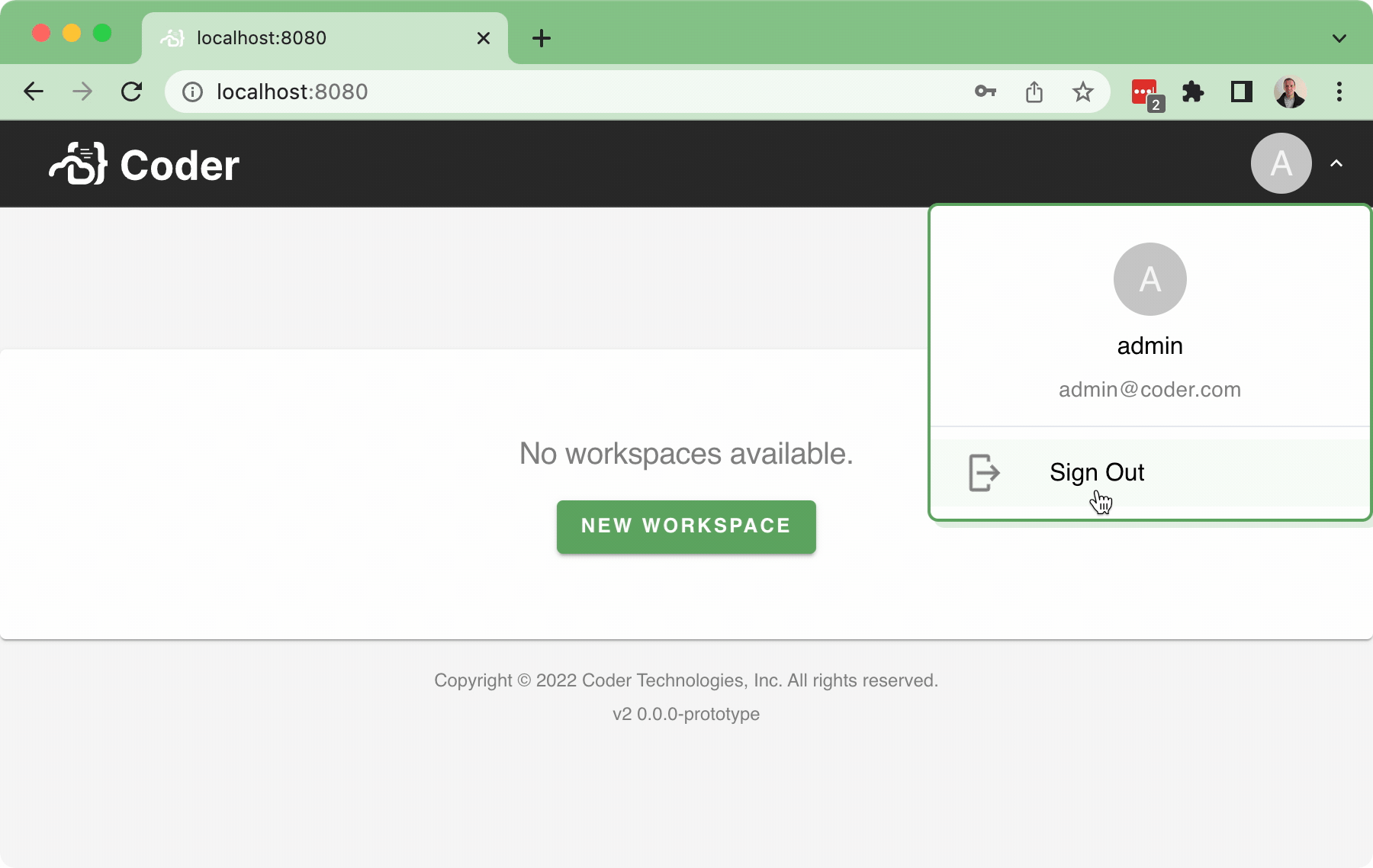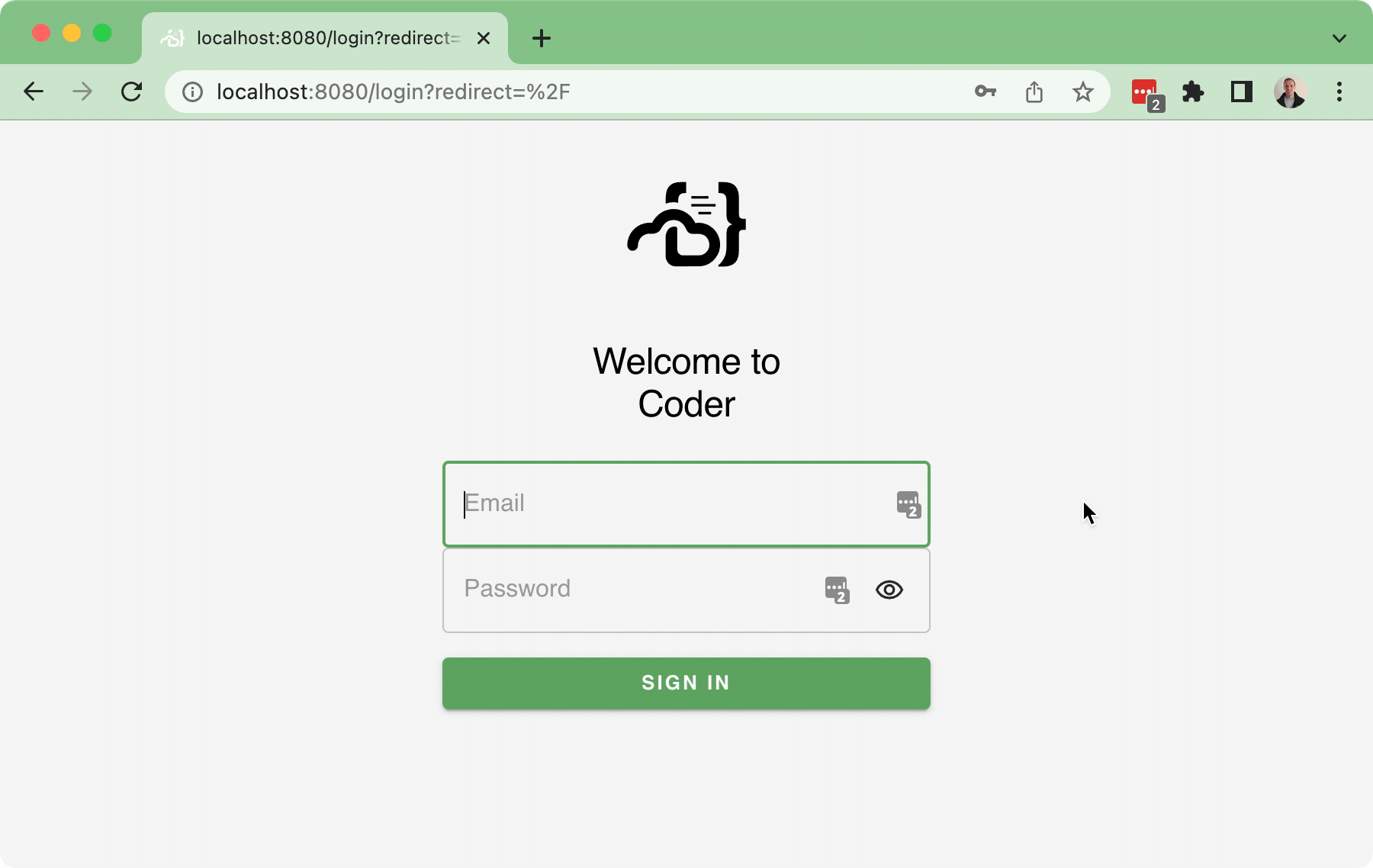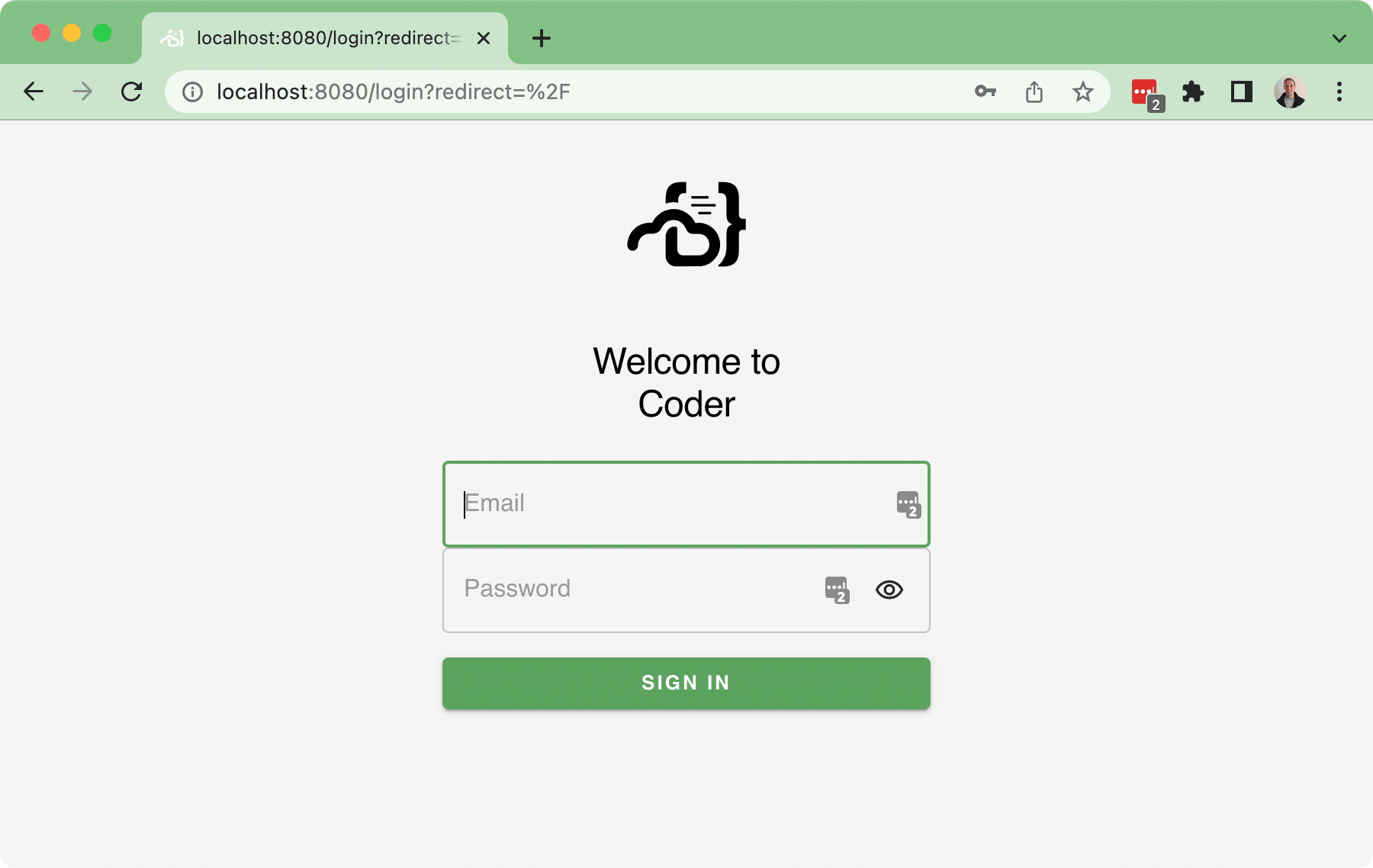 Bringing in a few pruned down components for the `<UserDropdown />` to integrate into the `<NavBar />`. In addition, this also implements a simple back-end API for `/logout` which just clears the session token.
107 lines
2.8 KiB
Go
107 lines
2.8 KiB
Go
package coderd_test
|
|
|
|
import (
|
|
"context"
|
|
"net/http"
|
|
"testing"
|
|
|
|
"github.com/stretchr/testify/require"
|
|
|
|
"github.com/coder/coder/coderd"
|
|
"github.com/coder/coder/coderd/coderdtest"
|
|
"github.com/coder/coder/httpmw"
|
|
)
|
|
|
|
func TestUsers(t *testing.T) {
|
|
t.Parallel()
|
|
|
|
t.Run("Authenticated", func(t *testing.T) {
|
|
t.Parallel()
|
|
server := coderdtest.New(t)
|
|
_ = server.RandomInitialUser(t)
|
|
_, err := server.Client.User(context.Background(), "")
|
|
require.NoError(t, err)
|
|
})
|
|
|
|
t.Run("CreateMultipleInitial", func(t *testing.T) {
|
|
t.Parallel()
|
|
server := coderdtest.New(t)
|
|
_ = server.RandomInitialUser(t)
|
|
_, err := server.Client.CreateInitialUser(context.Background(), coderd.CreateInitialUserRequest{
|
|
Email: "dummy@coder.com",
|
|
Organization: "bananas",
|
|
Username: "fake",
|
|
Password: "password",
|
|
})
|
|
require.Error(t, err)
|
|
})
|
|
|
|
t.Run("Login", func(t *testing.T) {
|
|
t.Parallel()
|
|
server := coderdtest.New(t)
|
|
user := server.RandomInitialUser(t)
|
|
_, err := server.Client.LoginWithPassword(context.Background(), coderd.LoginWithPasswordRequest{
|
|
Email: user.Email,
|
|
Password: user.Password,
|
|
})
|
|
require.NoError(t, err)
|
|
})
|
|
|
|
t.Run("LoginInvalidUser", func(t *testing.T) {
|
|
t.Parallel()
|
|
server := coderdtest.New(t)
|
|
_, err := server.Client.LoginWithPassword(context.Background(), coderd.LoginWithPasswordRequest{
|
|
Email: "hello@io.io",
|
|
Password: "wowie",
|
|
})
|
|
require.Error(t, err)
|
|
})
|
|
|
|
t.Run("LoginBadPassword", func(t *testing.T) {
|
|
t.Parallel()
|
|
server := coderdtest.New(t)
|
|
user := server.RandomInitialUser(t)
|
|
_, err := server.Client.LoginWithPassword(context.Background(), coderd.LoginWithPasswordRequest{
|
|
Email: user.Email,
|
|
Password: "bananas",
|
|
})
|
|
require.Error(t, err)
|
|
})
|
|
|
|
t.Run("ListOrganizations", func(t *testing.T) {
|
|
t.Parallel()
|
|
server := coderdtest.New(t)
|
|
_ = server.RandomInitialUser(t)
|
|
orgs, err := server.Client.UserOrganizations(context.Background(), "")
|
|
require.NoError(t, err)
|
|
require.Len(t, orgs, 1)
|
|
})
|
|
}
|
|
|
|
func TestLogout(t *testing.T) {
|
|
t.Parallel()
|
|
|
|
t.Run("LogoutShouldClearCookie", func(t *testing.T) {
|
|
t.Parallel()
|
|
|
|
server := coderdtest.New(t)
|
|
fullURL, err := server.URL.Parse("/api/v2/logout")
|
|
require.NoError(t, err, "Server URL should parse successfully")
|
|
|
|
req, err := http.NewRequestWithContext(context.Background(), http.MethodPost, fullURL.String(), nil)
|
|
require.NoError(t, err, "/logout request construction should succeed")
|
|
|
|
httpClient := &http.Client{}
|
|
|
|
response, err := httpClient.Do(req)
|
|
require.NoError(t, err, "/logout request should succeed")
|
|
response.Body.Close()
|
|
|
|
cookies := response.Cookies()
|
|
require.Len(t, cookies, 1, "Exactly one cookie should be returned")
|
|
|
|
require.Equal(t, cookies[0].Name, httpmw.AuthCookie, "Cookie should be the auth cookie")
|
|
require.Equal(t, cookies[0].MaxAge, -1, "Cookie should be set to delete")
|
|
})
|
|
}
|